For Windows, download HashiCorp Boundary Enterprise for free. Using identity-based security, you can access any system from any location without exposing your network.
An Examination of the HashiCorp Boundary Enterprise
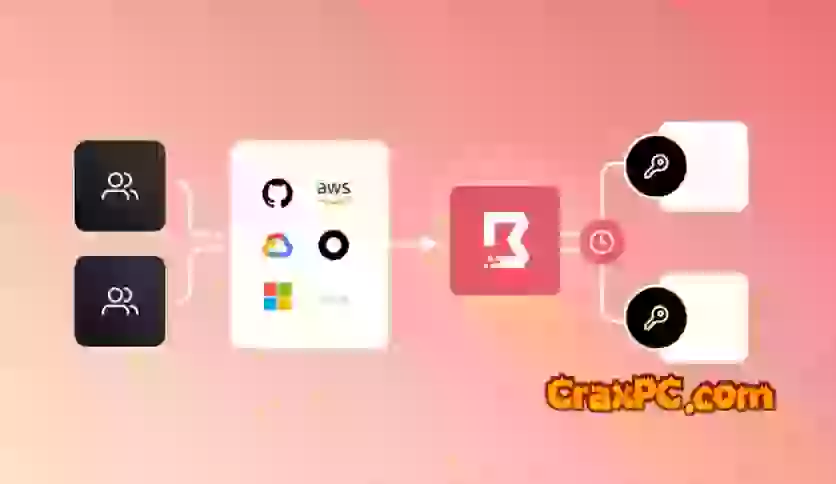
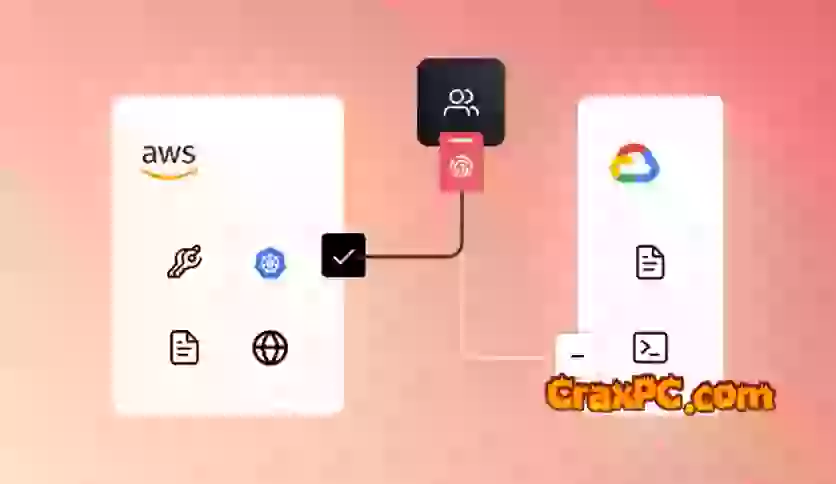
Ensuring secure access to infrastructure and applications across cloud, on-premises, and hybrid environments, it is an advanced access management solution. This functionality empowers organizations to establish and enforce access policies, manage user permissions, and centrally observe access activities.
Strengthened Security
A zero-trust security model is implemented to guarantee that resource access is exclusively granted on the basis of verified identity and additional contextual factors. By adopting this methodology, the potential for unauthorized entry is reduced, thereby fortifying the overall security stance.
Simplified Management of Access
Organizations can streamline their access management endeavors by integrating Boundary Enterprise into a solitary platform, thereby obviating the necessity to oversee numerous access control systems. This facilitates the streamlining of administrative duties and the enforcement of access policies.
Constant Scalability
It is intended to assist establishments of every scale. The software provides scalability and high availability functionalities, enabling organizations to adapt to expansion and maintain uninterrupted access control amidst dynamic environments.
Assurance of Auditability and Compliance
By providing comprehensive audit trails and access records, the platform facilitates the monitoring and evaluation of access activities for the purpose of ensuring compliance. This functionality facilitates compliance with regulatory obligations and, if required, aids forensic investigations.
Conditions of the System
Platforms supported: Windows 11, Windows 10
RAM (Memory): 2 GB; however, 4 GB is advised.
Free Space on the Hard Drive: 1 GB or more
To conclude,
HashiCorp Boundary Enterprise provides organizations with an all-encompassing access management solution that streamlines administration and places security first. Organizations have the ability to implement strong access controls, bolster their security stance, and efficiently fulfill compliance obligations.
Its audibility features and scalable architecture render it optimal for organizations in search of a streamlined, secure access management solution.