Akamai Technologies Infection Monkey for Windows is available for free download. This platform is an open-source breach and attack simulation (BAS) tool that evaluates the network infrastructure’s security posture. It enables you to simulate a variety of assault scenarios in order to identify defense vulnerabilities and gaps. It assists organizations in proactively bolstering their security measures and averting potential cyber threats; it is a potent instrument.
A Synopsis of Infection Monkey
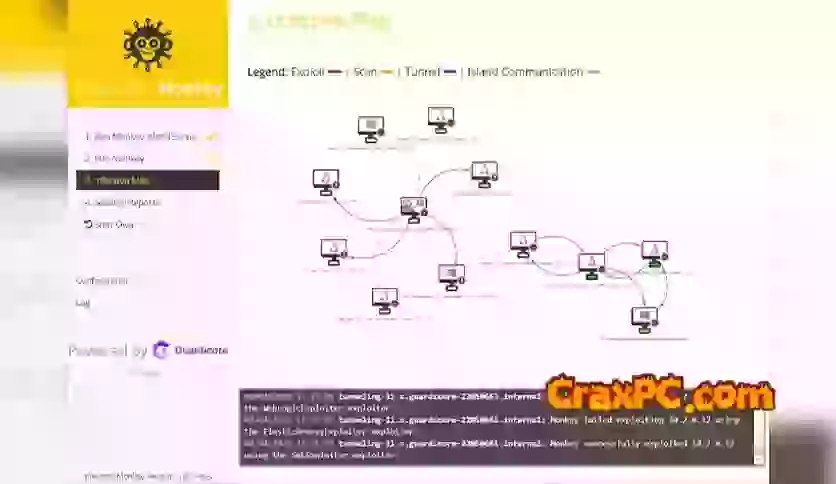
It functions through the implementation of a virtual chimpanzee in your network environment, which replicates the actions of a genuine assailant. This monkey then attempts to spread throughout the network by exploiting system and service vulnerabilities and misconfigurations. By doing so, organizations gain insight into the lateral movement patterns that a legitimate cyber adversary could employ to compromise sensitive data within their infrastructure.
Attack Simulation Scenarios
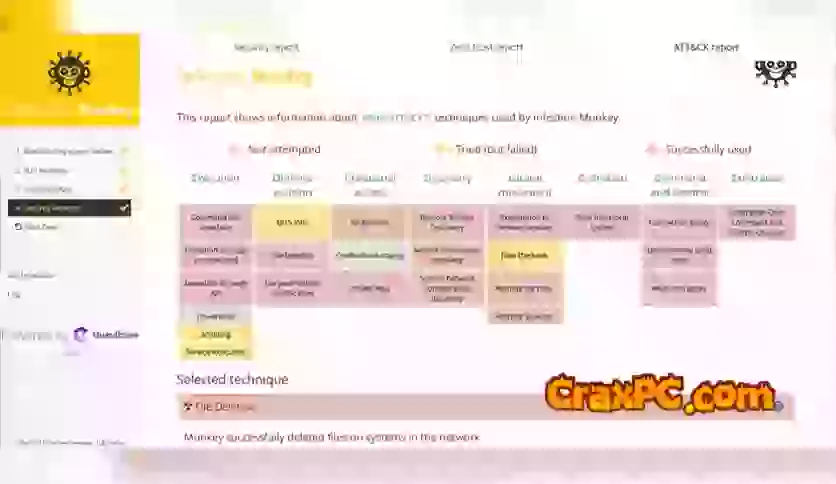
It is distinguished by its capacity to simulate an extensive variety of attack scenarios. The platform is capable of emulating a wide range of cybercriminal strategies, including phishing and brute-force. By conducting these simulations, organizations can detect vulnerabilities in their defenses and take proactive measures to patch them prior to actual attackers taking advantage of them.
Evaluation of Security Controls
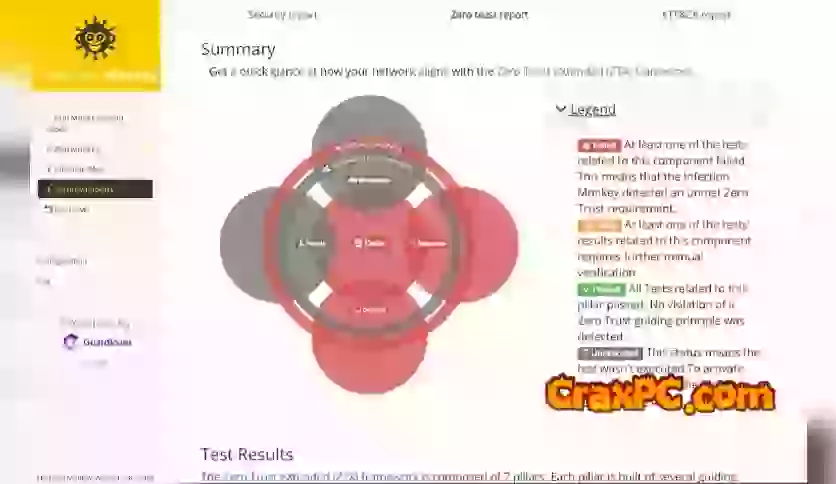
Additionally, it aids in assessing the efficacy of current security measures. Through simulated assaults, it attempts to circumvent firewalls, intrusion detection systems (IDS), and other security measures in order to evaluate their resilience. This enables organizations to detect vulnerabilities in their security infrastructure and subsequently enhance their defensive measures.
Real-Time Analysis and Reporting
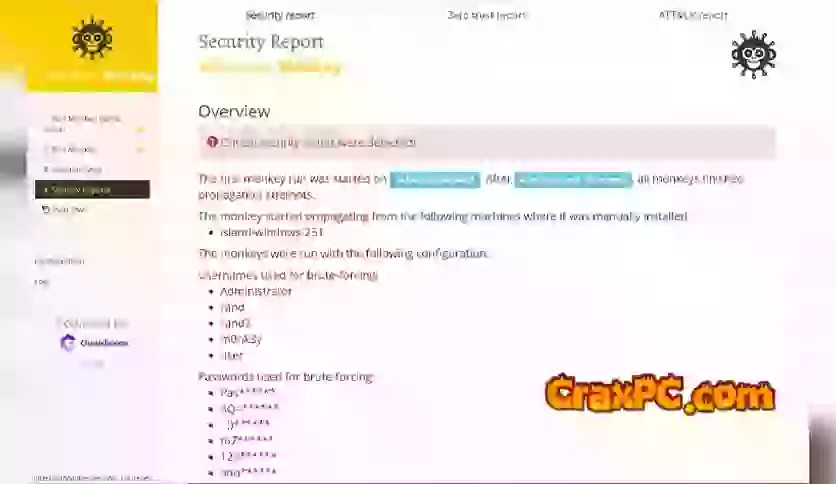
An additional benefit of employing it is its extensive capacity for reporting and analysis. Real-time feedback is furnished by the platform regarding the efficacy of its attack simulations, encompassing information regarding the compromised systems and the manner in which the attack spread. The provided information is of immense value to security teams as it allows them to more efficiently allocate resources and prioritize remediation endeavors.
Conditions of the System
System Operation: Windows 11/10/8.1/8/7
Processor speed of at least 1 GHz (2.4 GHz is suggested)
RAM: 2 GB (at least 4 GB is advised).
Free hard disk space of at least 200 MB is advised.
As a conclusion, Infection Monkey provides organizations seeking to strengthen their cybersecurity defenses with an indispensable resource. By conducting simulations of authentic attack scenarios and evaluating the efficacy of current security controls, organizations can detect and rectify weaknesses prior to their exploitation by malicious actors. Its robust capabilities and intuitive interface render it an essential acquisition for any organization that takes the protection of its digital assets seriously.